Carding
Professional
- Messages
- 2,870
- Reaction score
- 2,486
- Points
- 113
Experts found a flaw in the encryption scheme of the Key Group ransomware, which helped them develop a decryptor. Now malware victims will be able to restore their files to their previous state for free.
The decryption tool was created by specialists from EclecticIQ. According to the description, the decryptor works against the ransomware version, which dates back to the beginning of August.
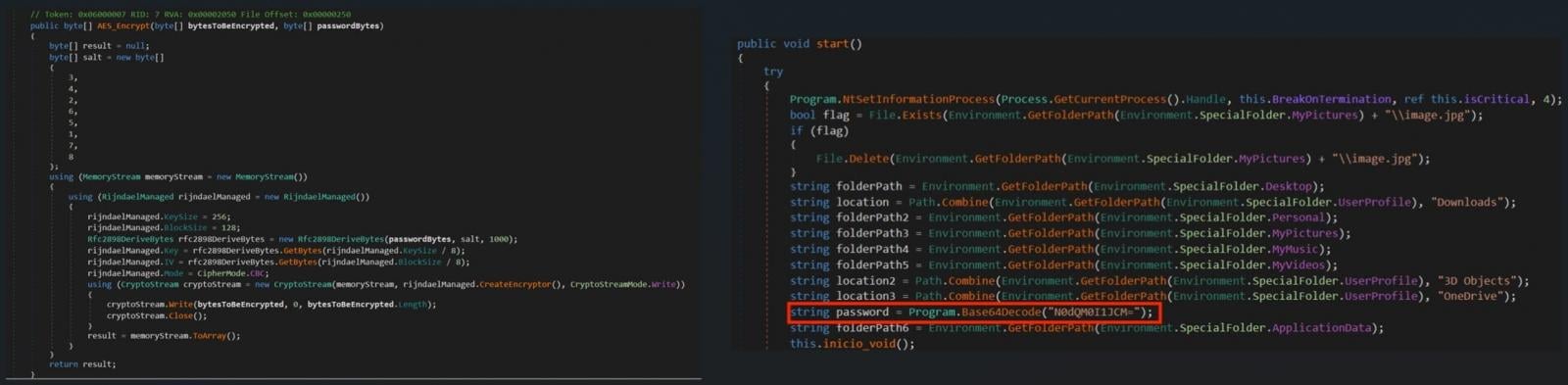
The authors of the Key Group have always claimed that their development uses military-grade AES encryption, but static salt is used at each stage of the malware's work. This approach makes the Key Group predictable and allows you to choose the key for decryption.
“The ransomware encrypts the victim’s data in Cipher Block Chaining (CBC) mode with a static password that is extracted from the key using Password-Based Key Derivation Function 2 (PBKDF2). The salt is fixed,” writes EclecticIQ in a blog post.
Key Group is a Russian-speaking group that has been active since the beginning of 2023. Malefactors attack organizations from different spheres, steal internal data, encrypt files and discuss ransom in Telegram channels.
The encryption process removes the original files and adds the .KEYGROUP777TG extension to the affected files. There is a suspicion that the authors of the Key Group used the Chaos 4.0 builder to develop their malware.
Cybercriminals use LOLBins to delete shadow copies. In addition, the ransomware modifies the host addresses of antivirus products to prevent them from updating.
The decryption tool was created by specialists from EclecticIQ. According to the description, the decryptor works against the ransomware version, which dates back to the beginning of August.
The authors of the Key Group have always claimed that their development uses military-grade AES encryption, but static salt is used at each stage of the malware's work. This approach makes the Key Group predictable and allows you to choose the key for decryption.
“The ransomware encrypts the victim’s data in Cipher Block Chaining (CBC) mode with a static password that is extracted from the key using Password-Based Key Derivation Function 2 (PBKDF2). The salt is fixed,” writes EclecticIQ in a blog post.

Key Group is a Russian-speaking group that has been active since the beginning of 2023. Malefactors attack organizations from different spheres, steal internal data, encrypt files and discuss ransom in Telegram channels.
The encryption process removes the original files and adds the .KEYGROUP777TG extension to the affected files. There is a suspicion that the authors of the Key Group used the Chaos 4.0 builder to develop their malware.
Cybercriminals use LOLBins to delete shadow copies. In addition, the ransomware modifies the host addresses of antivirus products to prevent them from updating.

