Mutt
Professional
- Messages
- 1,459
- Reaction score
- 1,245
- Points
- 113
Gal Weizman, an information security researcher, described the technical details of the High Grade Vulnerability (CVE-2019-18426) on WhatsApp. They allowed attackers to read files from Windows and macOS PCs and execute arbitrary code. The vulnerabilities are now fixed by the developer.
The flaws were found in the desktop versions of WhatsApp, as well as in the web version of the application. They allowed hackers to remotely access user files and send a specially crafted message, similar to code, which could be viewed to execute arbitrary code in the context of the WhatsApp web domain.
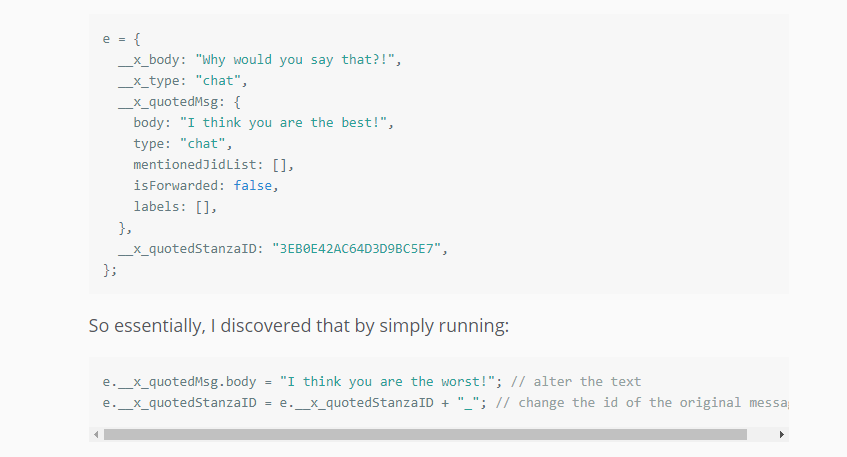
Weizman was able to change the text of someone else's reply to a message using a line of code with metadata:
Then he created a message that looked like a normal preview message, but instead redirected to a different domain with a simple link substitution.
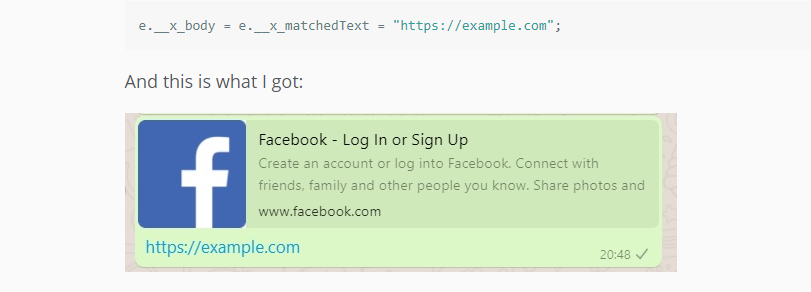
The link may look less obvious:

This works thanks to the role of @ in the URL specification. The purpose of @ in URLs is to pass the username and password for the visited domains like this: https: // USERNAME: PASSWORD@DOMAIN.COM. It is possible to abuse this and replace the username and password with something else: https://DOMAIN-A.COM@DOMAIN-B.com and it will still work. Firefox is the only browser that, by default, warns users if this method is used without specifying a username and password.
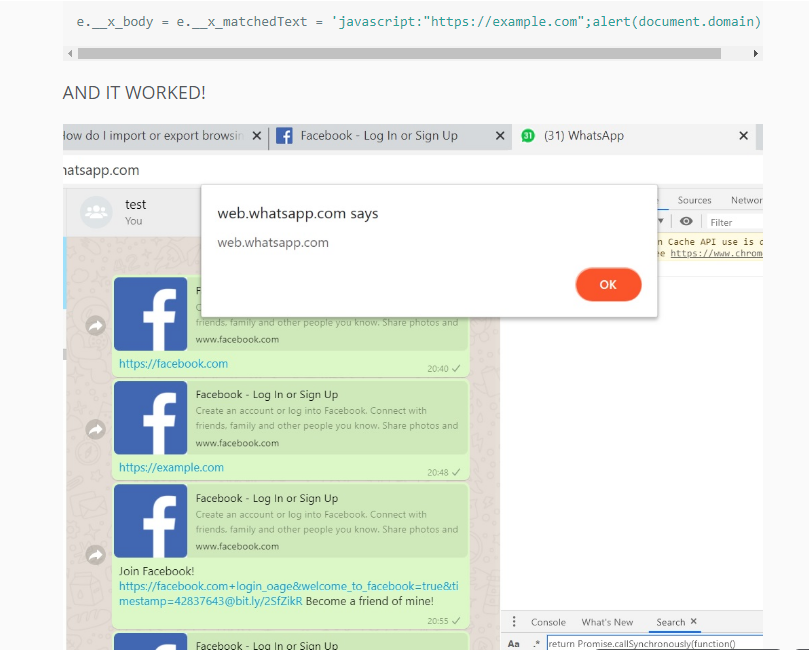
And here's an example using javascript: URI:
An improperly configured Content Security Policy (CSP) in the web domain allowed cross-site scripting with an iframe from a separate resource.
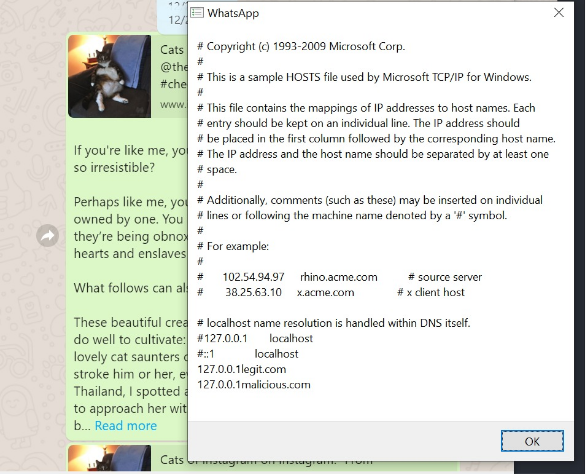
Weizman also checked the vulnerabilities of the messenger to gain rights to remotely read files inside the attacked system.
The researcher reported the vulnerabilities he discovered in 2019. After that, the Facebook security service released a corresponding update. The researcher received $ 12,500 as a reward.
Earlier, the Israeli company Check Point published a study of a vulnerability that allowed attackers to block WhatsApp from the devices of those with whom they were in the same group chat. Hackers could enter a pre-selected group chat and change certain parameters as a member, and then send malicious messages using Whatsapp Web and a web browser debugging tool. Thus, the attackers launched a vicious circle of failures for all members of the group chat, which denied them access to all functions of the messenger. Users deleted and re-downloaded WhatsApp, but could not return to the chat. To break the vicious circle of errors, they had to eventually delete the chat itself. To date, the problem has been resolved in versions of the application higher than 2.19.246.
Thanks for attention!
The flaws were found in the desktop versions of WhatsApp, as well as in the web version of the application. They allowed hackers to remotely access user files and send a specially crafted message, similar to code, which could be viewed to execute arbitrary code in the context of the WhatsApp web domain.
Weizman was able to change the text of someone else's reply to a message using a line of code with metadata:

Then he created a message that looked like a normal preview message, but instead redirected to a different domain with a simple link substitution.

The link may look less obvious:

This works thanks to the role of @ in the URL specification. The purpose of @ in URLs is to pass the username and password for the visited domains like this: https: // USERNAME: PASSWORD@DOMAIN.COM. It is possible to abuse this and replace the username and password with something else: https://DOMAIN-A.COM@DOMAIN-B.com and it will still work. Firefox is the only browser that, by default, warns users if this method is used without specifying a username and password.
And here's an example using javascript: URI:

An improperly configured Content Security Policy (CSP) in the web domain allowed cross-site scripting with an iframe from a separate resource.

Weizman also checked the vulnerabilities of the messenger to gain rights to remotely read files inside the attacked system.
The researcher reported the vulnerabilities he discovered in 2019. After that, the Facebook security service released a corresponding update. The researcher received $ 12,500 as a reward.
Earlier, the Israeli company Check Point published a study of a vulnerability that allowed attackers to block WhatsApp from the devices of those with whom they were in the same group chat. Hackers could enter a pre-selected group chat and change certain parameters as a member, and then send malicious messages using Whatsapp Web and a web browser debugging tool. Thus, the attackers launched a vicious circle of failures for all members of the group chat, which denied them access to all functions of the messenger. Users deleted and re-downloaded WhatsApp, but could not return to the chat. To break the vicious circle of errors, they had to eventually delete the chat itself. To date, the problem has been resolved in versions of the application higher than 2.19.246.
Thanks for attention!
