Brother
Professional
- Messages
- 2,590
- Reaction score
- 526
- Points
- 113
Will the company pay a fabulous ransom for its customers data?
The Kansas City Area Transportation Authority (KCATA), a key public transportation operator in Kansas City, Missouri, USA, has been hit by a massive cyberattack . The incident occurred on January 23 of this year.
KCATA serves metro and 78 bus routes in seven counties in Missouri and Kansas. As of 2022, the company's total passenger traffic was more than 10.5 million people.
The very next day after the attack, KCATA issued a statement announcing the launch of an investigation involving external experts and informing the relevant authorities, including the FBI.
According to the company's representatives, the cyberattack did not affect the operation of transport services, including bus routes and paratransit services. However, it led to disruptions in the work of regional call centers.
The Medusa hacker group quickly claimed responsibility for the attack. It threatens to publish all the stolen data unless KCATA pays a $ 2 million ransom. In addition, hackers offer the possibility of deferred payment for an additional 100 thousand dollars a day.
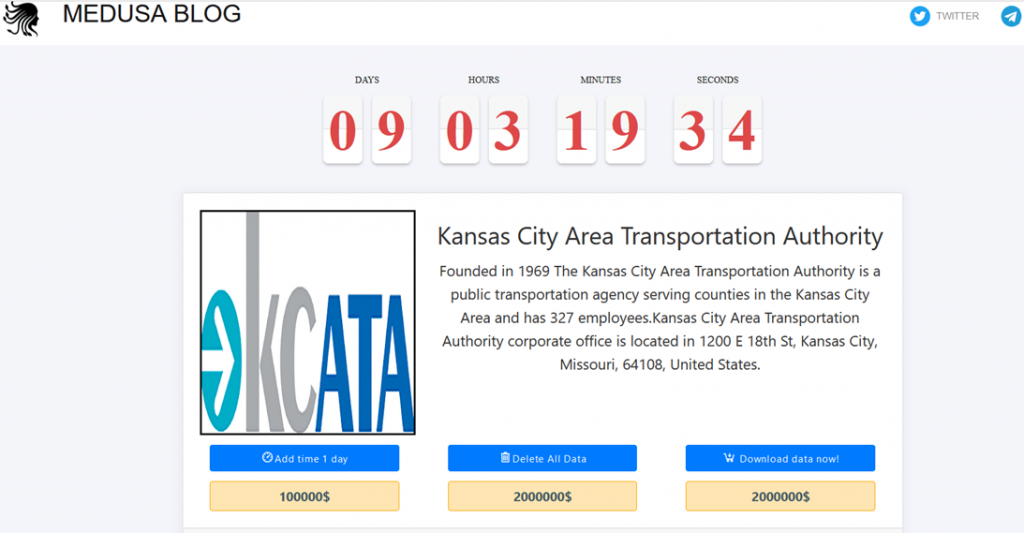
So far, KCATA has not disclosed any details about the attack, including information about the family of ransomware used or confirmation of the data leak. However, Medusa posted samples of the data allegedly stolen from KCATA on its Tor network site as proof of hacking.
The incident highlights the growing threat that cybercriminals pose to urban infrastructure and public services. Let's see what the attacked KCATA will do now. Although it is unlikely that there will be an extra two million dollars in the budget of Kansas City. Moreover, the nature of the stolen data can hardly be called highly sensitive information.
The Kansas City Area Transportation Authority (KCATA), a key public transportation operator in Kansas City, Missouri, USA, has been hit by a massive cyberattack . The incident occurred on January 23 of this year.
KCATA serves metro and 78 bus routes in seven counties in Missouri and Kansas. As of 2022, the company's total passenger traffic was more than 10.5 million people.
The very next day after the attack, KCATA issued a statement announcing the launch of an investigation involving external experts and informing the relevant authorities, including the FBI.
According to the company's representatives, the cyberattack did not affect the operation of transport services, including bus routes and paratransit services. However, it led to disruptions in the work of regional call centers.
The Medusa hacker group quickly claimed responsibility for the attack. It threatens to publish all the stolen data unless KCATA pays a $ 2 million ransom. In addition, hackers offer the possibility of deferred payment for an additional 100 thousand dollars a day.

So far, KCATA has not disclosed any details about the attack, including information about the family of ransomware used or confirmation of the data leak. However, Medusa posted samples of the data allegedly stolen from KCATA on its Tor network site as proof of hacking.
The incident highlights the growing threat that cybercriminals pose to urban infrastructure and public services. Let's see what the attacked KCATA will do now. Although it is unlikely that there will be an extra two million dollars in the budget of Kansas City. Moreover, the nature of the stolen data can hardly be called highly sensitive information.
