Carding
Professional
- Messages
- 2,870
- Reaction score
- 2,486
- Points
- 113
Massive cyber attacks have put Chinese businesses in the hands of hackers.
Cybersecurity company Proofpoint reports that Chinese companies on the mainland have been targeted by cybercriminals, many of whom use new types of malware. Analysts said that in 2023, about 30 such campaigns were detected in China.
The attacks involve imitating Chinese companies by attackers who use phishing or social engineering to persuade unsuspecting employees to install malware.
Campaigns distribute the following malware:
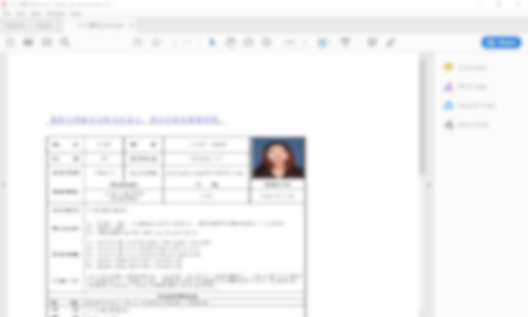
Example of a decoy document that loadsValleyRAT
It is assumed that different groups are behind the campaigns. It is not known whether they interact with each other and exchange tools and experience. Proofpoint analysts do not draw conclusions about the motives of cyber attacks and do not indicate where the threat groups originate, but they assume that the victims of hackers are located on the Chinese mainland.
Proofpoint emphasizes that campaigns are not large-scale and are usually aimed at international organizations operating in China. Email topics and content are usually written in Chinese and are related to business topics such as invoices, payments, and new products.
Almost a decade after Edward Snowden's leaked documents revealed that the NSA hacked the servers of Chinese telecommunications giant Huawei, Beijing has officially acknowledged the attack. According to Beijing, the NSA "systematically conducted attacks" on China in an attempt to steal "important data."
In turn, the director of the US FBI Chris Uray said that China's cyber espionage program is so extensive that it surpasses all similar programs of other major countries combined. The FBI director's comments were unusually harsh, even amid longstanding U.S. concerns about Chinese hackers.
Cybersecurity company Proofpoint reports that Chinese companies on the mainland have been targeted by cybercriminals, many of whom use new types of malware. Analysts said that in 2023, about 30 such campaigns were detected in China.
The attacks involve imitating Chinese companies by attackers who use phishing or social engineering to persuade unsuspecting employees to install malware.
Campaigns distribute the following malware:
- The ValleyRAT Remote Access Trojan (RAT), written in C++ and compiled in Chinese, demonstrates the functions of a typical RAT Trojan. Most of the campaigns distributing ValleyRAT were conducted in Chinese, and mostly used fake payment invoices associated with various Chinese companies;
- A new variant of Gh0stRAT, which Proofpoint calls Sainbox. Almost all campaigns using Sainbox used a decoy document in the form of a payment invoice;
- Purple Fox malware that was detected in three campaigns and also used against Japanese targets. The malware has rootkit and backdoor capabilities and is used as a loader for other malicious programs.

Example of a decoy document that loadsValleyRAT
It is assumed that different groups are behind the campaigns. It is not known whether they interact with each other and exchange tools and experience. Proofpoint analysts do not draw conclusions about the motives of cyber attacks and do not indicate where the threat groups originate, but they assume that the victims of hackers are located on the Chinese mainland.
Proofpoint emphasizes that campaigns are not large-scale and are usually aimed at international organizations operating in China. Email topics and content are usually written in Chinese and are related to business topics such as invoices, payments, and new products.
Almost a decade after Edward Snowden's leaked documents revealed that the NSA hacked the servers of Chinese telecommunications giant Huawei, Beijing has officially acknowledged the attack. According to Beijing, the NSA "systematically conducted attacks" on China in an attempt to steal "important data."
In turn, the director of the US FBI Chris Uray said that China's cyber espionage program is so extensive that it surpasses all similar programs of other major countries combined. The FBI director's comments were unusually harsh, even amid longstanding U.S. concerns about Chinese hackers.

