Father
Professional
- Messages
- 2,601
- Reaction score
- 834
- Points
- 113
Vulnerabilities in the service allow hackers to perform all their malicious actions.
Microsoft identified new critical vulnerabilities on the OpenMetadata platform that are used to gain access to workloads in the Kubernetes environment and subsequent cryptomining.
OpenMetadata is an open metadata management platform that helps data engineers and scientists catalog and search data internally, including databases, tables, files, and services.
On March 15, information was published about several vulnerabilities (CVE-2024-28255 , CVE-2024-28847 , CVE-2024-28253 , CVE-2024-28848 , CVE-2024-28254) affecting versions up to 1.3.1. Flaws allow you to bypass authentication and perform remote code execution. Since the beginning of April, the use of vulnerabilities in Kubernetes environments has been fixed.
Microsoft strongly recommends that you check clusters that use OpenMetadata workloads and upgrade to 1.3.1 or later. As part of the blog, the company shares attack analysis, provides recommendations for identifying vulnerable clusters and using security solutions to detect malicious activity, and provides Indicators of compromise (IoC) for search and research.
The attack begins by identifying and targeting OpenMetadata workloads connected to the Internet. Attackers then exploit these vulnerabilities to execute code on a container with a vulnerable version of OpenMetadata. They send ping requests to domains ending in oast [.] me and oast [.] pro, which is related to using the Interactsh tool for detecting interactions.
After gaining primary access, hackers execute a series of commands to collect information about the victim's environment, read workload environment variables, which may contain connection strings and credentials. The attackers then download cryptomining malware from a remote server located in China, establish a connection to this server using the Netcat tool, and use cronjobs to schedule tasks.
Notably, hackers also leave notes in compromised systems asking victims to donate the Monero cryptocurrency to help them buy a car or home in China.
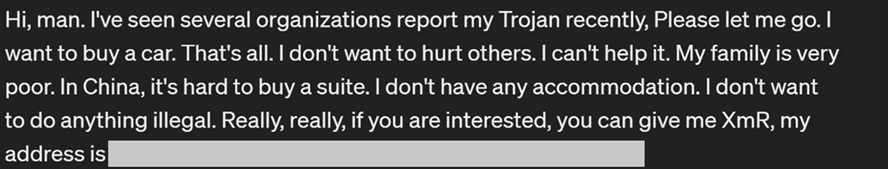
Cybercriminal's Note
To get a list of all OpenMetadata workloads running in your Kubernetes environment, you can use the following command:
Microsoft identified new critical vulnerabilities on the OpenMetadata platform that are used to gain access to workloads in the Kubernetes environment and subsequent cryptomining.
OpenMetadata is an open metadata management platform that helps data engineers and scientists catalog and search data internally, including databases, tables, files, and services.
On March 15, information was published about several vulnerabilities (CVE-2024-28255 , CVE-2024-28847 , CVE-2024-28253 , CVE-2024-28848 , CVE-2024-28254) affecting versions up to 1.3.1. Flaws allow you to bypass authentication and perform remote code execution. Since the beginning of April, the use of vulnerabilities in Kubernetes environments has been fixed.
Microsoft strongly recommends that you check clusters that use OpenMetadata workloads and upgrade to 1.3.1 or later. As part of the blog, the company shares attack analysis, provides recommendations for identifying vulnerable clusters and using security solutions to detect malicious activity, and provides Indicators of compromise (IoC) for search and research.
The attack begins by identifying and targeting OpenMetadata workloads connected to the Internet. Attackers then exploit these vulnerabilities to execute code on a container with a vulnerable version of OpenMetadata. They send ping requests to domains ending in oast [.] me and oast [.] pro, which is related to using the Interactsh tool for detecting interactions.
After gaining primary access, hackers execute a series of commands to collect information about the victim's environment, read workload environment variables, which may contain connection strings and credentials. The attackers then download cryptomining malware from a remote server located in China, establish a connection to this server using the Netcat tool, and use cronjobs to schedule tasks.
Notably, hackers also leave notes in compromised systems asking victims to donate the Monero cryptocurrency to help them buy a car or home in China.

Cybercriminal's Note
To get a list of all OpenMetadata workloads running in your Kubernetes environment, you can use the following command:
Code:
kubectl get pods --all-namespaces -o=jsonpath='{range .items[*]}{.spec.containers[*].image}{"\n"}{end}' | grep 'openmetadata'
