Brother
Professional
- Messages
- 2,590
- Reaction score
- 526
- Points
- 113
In the new iteration, the banking Trojan has received qualitatively new attack capabilities.
Cybersecurity researchers discovered a new version of the Android Trojan for Android called Chameleon, which is aimed primarily at European users of banking applications.
The new version of the mobile malware has been able to control infected devices using the Android accessibility service, and has also significantly expanded its attack geography.
Chameleon was first spotted in April 2023 by Cyble. Then experts noted that the malware is mainly aimed at users from Australia and Poland, but now Italy and the United Kingdom have joined the vulnerable countries.
It is noteworthy that even at that time, the Trojan had the ability to use access to the Android accessibility service, albeit for very limited scenarios such as collecting confidential data and conducting overlay attacks.
In previous iterations, fake malware applications containing Chameleon were placed on phishing pages and often disguised as clients of official agencies, such as the Australian Taxation Office, or large online services, such as the cryptocurrency trading platform CoinSpot.
ThreatFabric notes that Chameleon is now distributed through the DaaS service Zombinder, which links malware to legitimate applications. Despite speculation that Tinder would be shut down this year, it resurfaced online last month, offering attackers new ways to bypass Android restrictions for installing malware.
The main feature of the updated version of Chameleon, as noted earlier, is the ability to fully capture the device through the Android special features service. Thus, hackers can perform absolutely any unauthorized actions on behalf of the victim, as long as the victim does not see malicious activity.
The Trojan checks the operating system version on the device and, if it detects Android 13 or higher, prompts the victim to enable the necessary settings. This loads an HTML page that looks quite legitimate and guides the user step-by-step in the process of activating the special features service.
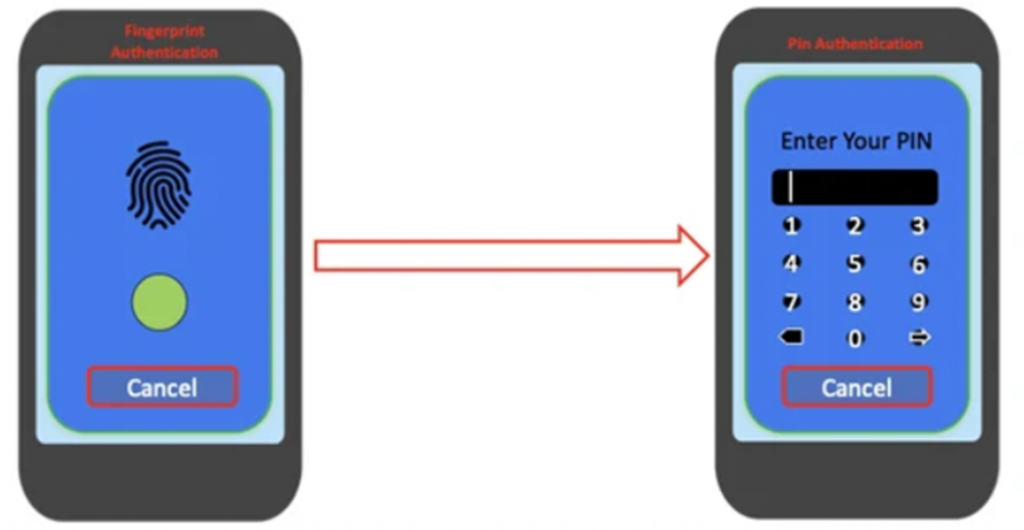
Another notable innovation of Chameleon is the use of the Android API to cancel a biometrics request on the target device. This is done by switching the authentication mechanism to a PIN code, which allows the Trojan to easily unlock the compromised device at any time.
The update of the banking Trojan described above is another reminder that cybercriminals are constantly improving their tools and methods of attacking mobile devices.
This situation clearly demonstrates how important it is for users to be vigilant — carefully check the reputation of unknown applications, monitor the requested permissions, and do not grant sensitive access unnecessarily. Well, installing a mobile antivirus will also be useful.
Cybersecurity researchers discovered a new version of the Android Trojan for Android called Chameleon, which is aimed primarily at European users of banking applications.
The new version of the mobile malware has been able to control infected devices using the Android accessibility service, and has also significantly expanded its attack geography.
Chameleon was first spotted in April 2023 by Cyble. Then experts noted that the malware is mainly aimed at users from Australia and Poland, but now Italy and the United Kingdom have joined the vulnerable countries.
It is noteworthy that even at that time, the Trojan had the ability to use access to the Android accessibility service, albeit for very limited scenarios such as collecting confidential data and conducting overlay attacks.
In previous iterations, fake malware applications containing Chameleon were placed on phishing pages and often disguised as clients of official agencies, such as the Australian Taxation Office, or large online services, such as the cryptocurrency trading platform CoinSpot.
ThreatFabric notes that Chameleon is now distributed through the DaaS service Zombinder, which links malware to legitimate applications. Despite speculation that Tinder would be shut down this year, it resurfaced online last month, offering attackers new ways to bypass Android restrictions for installing malware.
The main feature of the updated version of Chameleon, as noted earlier, is the ability to fully capture the device through the Android special features service. Thus, hackers can perform absolutely any unauthorized actions on behalf of the victim, as long as the victim does not see malicious activity.
The Trojan checks the operating system version on the device and, if it detects Android 13 or higher, prompts the victim to enable the necessary settings. This loads an HTML page that looks quite legitimate and guides the user step-by-step in the process of activating the special features service.
Another notable innovation of Chameleon is the use of the Android API to cancel a biometrics request on the target device. This is done by switching the authentication mechanism to a PIN code, which allows the Trojan to easily unlock the compromised device at any time.

The update of the banking Trojan described above is another reminder that cybercriminals are constantly improving their tools and methods of attacking mobile devices.
This situation clearly demonstrates how important it is for users to be vigilant — carefully check the reputation of unknown applications, monitor the requested permissions, and do not grant sensitive access unnecessarily. Well, installing a mobile antivirus will also be useful.
