Carding Forum
Professional
- Messages
- 2,788
- Reaction score
- 1,297
- Points
- 113
The activity of APT40 spies was the reason for the warning of leading information security agencies.
Eight leading cybersecurity agencies issued a joint warning about the activities of the Chinese cyber espionage group APT40, which is able to exploit vulnerabilities in software just a few hours or days after detection.
APT40 (Bronze Mohawk, Gingham Typhoon, Kryptonite Panda, Leviathan, Red Ladon, TA423) has been operating since 2013. The main targets of the attacks are located in the Asia-Pacific region. The hacker group is believed to be based in Haikou and operates under the auspices of the Chinese Ministry of State Security (MSS).
In July 2021, the UK attributed APT40 to the Chinese government. Several members of the group were charged with a multi-year campaign to steal trade secrets, intellectual property and valuable information from various sectors.
APT40 Group s) Chart
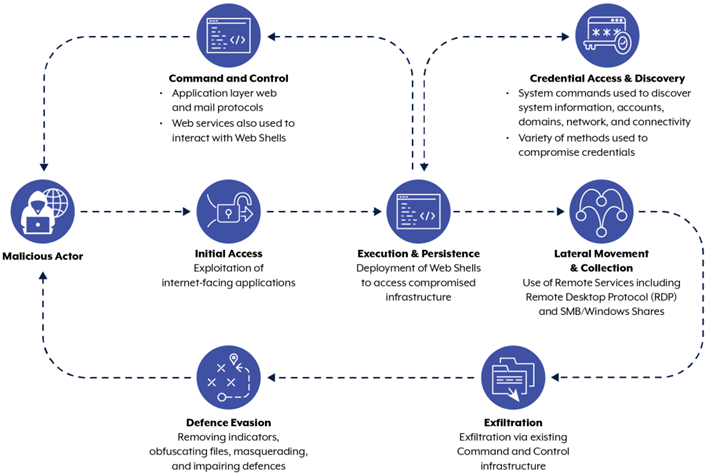
APT40 actively monitors new vulnerabilities in widely used software such as Log4j, Atlassian Confluence, and Microsoft Exchange. The group regularly scouts the networks of various countries to find vulnerable devices and quickly implement exploits.
An important feature of the group's tactics is the use of web shells to establish and maintain access to the victim's environment, as well as the use of Australian sites as a C2 server. The group also includes legacy or non-updated devices, such as SOHO routers, in its infrastructure to redirect malicious traffic and avoid detection. This style of operation is also typical for other Chinese groups, such as Volt Typhoon.
APT40 has been linked to several waves of attacks over the past few years. These include the use of the ScanBox framework for intelligence and exploiting a vulnerability in WinRAR ( CVE-2023-38831, CVSS score: 7.8).
According to Mandiant, APT40's activities are part of China's broad trend in cyber espionage, aimed at increasing stealth. Hacker groups are increasingly using Edge of Network (Edge Computing) devices, ORB networks ( Operational Relay Box), and LotL ( Living off the Land) techniques to stay undetected.
To reduce the risks associated with APT40 threats, organizations are advised to:
These measures will help organizations protect themselves from the growing threat from APT40 and other similar hacker groups, giving them more time to identify and neutralize potential attacks.
Source
Eight leading cybersecurity agencies issued a joint warning about the activities of the Chinese cyber espionage group APT40, which is able to exploit vulnerabilities in software just a few hours or days after detection.
APT40 (Bronze Mohawk, Gingham Typhoon, Kryptonite Panda, Leviathan, Red Ladon, TA423) has been operating since 2013. The main targets of the attacks are located in the Asia-Pacific region. The hacker group is believed to be based in Haikou and operates under the auspices of the Chinese Ministry of State Security (MSS).
In July 2021, the UK attributed APT40 to the Chinese government. Several members of the group were charged with a multi-year campaign to steal trade secrets, intellectual property and valuable information from various sectors.

APT40 Group s) Chart
APT40 actively monitors new vulnerabilities in widely used software such as Log4j, Atlassian Confluence, and Microsoft Exchange. The group regularly scouts the networks of various countries to find vulnerable devices and quickly implement exploits.
An important feature of the group's tactics is the use of web shells to establish and maintain access to the victim's environment, as well as the use of Australian sites as a C2 server. The group also includes legacy or non-updated devices, such as SOHO routers, in its infrastructure to redirect malicious traffic and avoid detection. This style of operation is also typical for other Chinese groups, such as Volt Typhoon.
APT40 has been linked to several waves of attacks over the past few years. These include the use of the ScanBox framework for intelligence and exploiting a vulnerability in WinRAR ( CVE-2023-38831, CVSS score: 7.8).
According to Mandiant, APT40's activities are part of China's broad trend in cyber espionage, aimed at increasing stealth. Hacker groups are increasingly using Edge of Network (Edge Computing) devices, ORB networks ( Operational Relay Box), and LotL ( Living off the Land) techniques to stay undetected.
To reduce the risks associated with APT40 threats, organizations are advised to:
- Maintain adequate logging mechanisms;
- Implement multi-factor authentication (MFA);
- Implement a robust patch management system;
- Replace outdated equipment;
- Disable unused services, ports, and protocols;
- Segment networks to prevent access to sensitive data.
These measures will help organizations protect themselves from the growing threat from APT40 and other similar hacker groups, giving them more time to identify and neutralize potential attacks.
Source
